There are two main types of encryption
1. Asymmetric Encryption
2. Symmetric Encryption
.
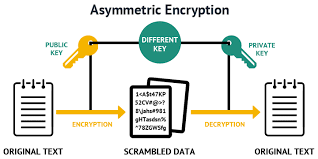
1.1 Asymmetric Encryption or Public-key cryptography -
is a encryption system that uses pairs of keys: public keys, which may be disseminated widely, and private keys,
which are known only to the owner.Message is encrypted with a recipient's public key and cannot be decrypted
by anyone who does not possess the matching private key, who is thus presumed to be the owner of that key and the person associated with the public key.
This is used in an attempt to ensure confidentiality. Effective security only requires keeping the private key private; the public key can be openly
distributed without compromising security
In such a system, any person can encrypt a message using the receiver's public key, but that encrypted message can only be decrypted with the receiver's private key.
This allows, for instance, a server to generate a cryptographic key intended for symmetric-key cryptography,
then use a client's openly-shared public key to encrypt that newly-generated symmetric key. Now, the server can send this encrypted symmetric key
on insecure channels to the client, and only the client can decrypt it using the client's private key pair to the public key used by the server
to encrypt this message. With the client and server both having the same symmetric key now, they can safely transition to symmetric key
encryption to securely communicate back and forth on otherwise-insecure channels. This has the advantage of not having to manually pre-share symmetric keys,
while also gaining the higher data throughput advantage of symmetric-key cryptography over asymmetric key cryptography.
A very good example of public key encryption is Digital signatures, here, Message is signed with the sender's private key and can
be verified by anyone who has access to the sender's public key. This verification proves that the sender had access to the private key,
and therefore is likely to be the person associated with the public key. This also ensures that the message has not been tampered with,
as a signature is mathematically bound to the message it originally was made with, and verification will fail for practically any other message,
no matter how similar to the original message.
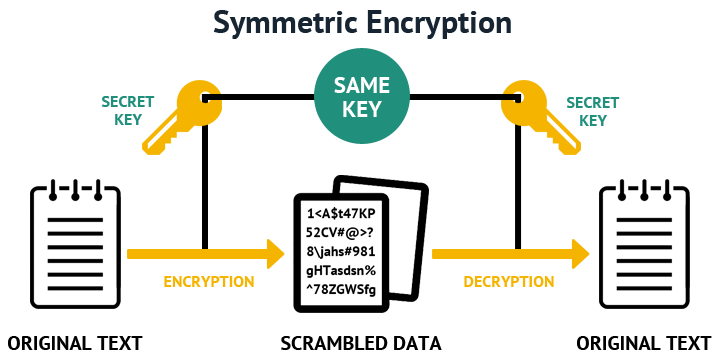
1.2 Symmetric-key algorithms - are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and
decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys. The keys, in practice, represent
a shared secret between two or more parties that can be used to maintain a private information link. This requirement that both parties have access to
the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key encryption (also known as asymmetric key encryption).
It’s time to take a closer look at the symmetric encryption process. To understand how symmetric cryptography works,
you need to know what the components are that are involved in the process:
| Symmetric Encryption | Asymmetric Encryption | |
|---|---|---|
| The Basics | Symmetric encryption makes use of a single key for both encryption and decryption. | Asymmetric encryption uses different keys for encryption and decryption. It applies a public key for encryption, while a private key is used for decryption. |
| Algorithms | Symmetric encryption using algorithms like 3DES, DES, RC4, AES and QUAD. | Whereas, Asymmetric encryption uses RSA and ECC algorithms to create the public and private keys. |
| Performance | While Symmetric encryption is fast in its execution. | Asymmetric encryption tends to be slower in execution as a result of more complex algorithms which come with a high computation burden. |
| Purpose | Symmetric encryption is utilized for bulk data transmission. | Asymmetric encryption is mostly used for securely exchanging secret keys. |